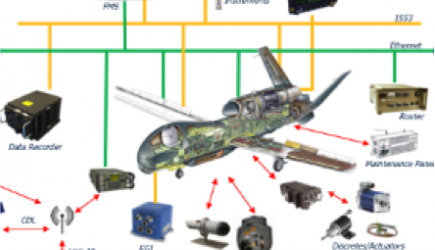
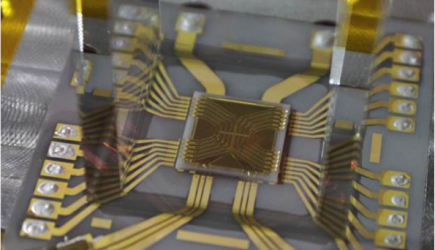
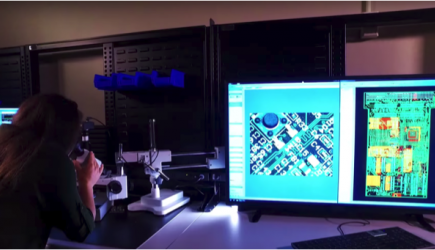
Cybersecurity, Information Protection, and Hardware Evaluation Research
The Cybersecurity, Information Protection, and Hardware Evaluation Research Laboratory is a leader in developing the technologies that secure, defend, and respond to threats within our country’s information, distribution, and network systems.
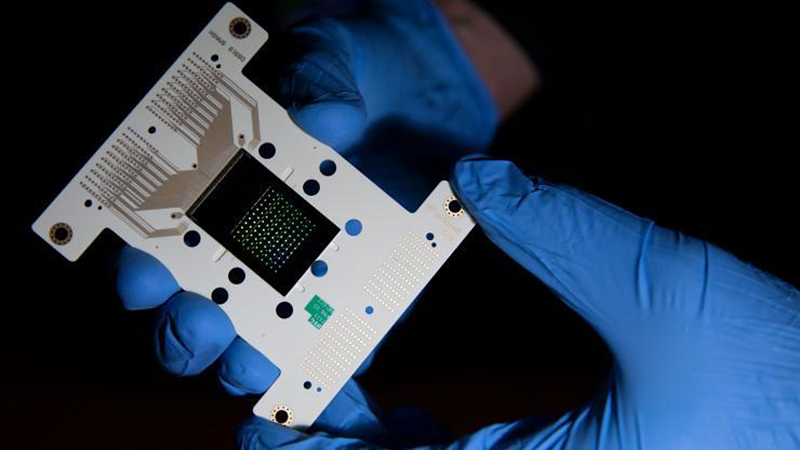
CIPHER provides high-impact solutions to some of today’s most challenging cybersecurity problems, while also turning revolutionary concepts and breakthrough technologies into practical capabilities to address future threats. CIPHER engineers and scientists develop and deploy cutting-edge technologies in computing, network architectures, signal and protocol analysis, hardware security and trust, assured software and algorithms, network forensics, malware analysis, hardware and software reverse engineering, and advanced analytics.
Georgia Tech Campus Collaboration
CIPHER researchers collaborate extensively with Georgia Tech faculty and students and CIPHER employs and trains numerous Georgia Tech students on real-world problems. CIPHER faculty teach classes in multiple departments at the undergraduate and graduate levels and GTRI offers a range of Cyber Security Professional Education courses.
External Collaboration
CIPHER collaborates with outside partners in industry, government, and academia. CIPHER has hosted academic researchers and government employees for extended periods of time for cybersecurity research and training opportunities. In addition, CIPHER researchers have worked in government facilities to provide expertise across a range of technical areas.
Professional Education, Outreach and Awareness
CIPHER cybersecurity experts provide tailored educational opportunities, hacker competitions, emerging threat conferences, threat landscape reports, and other outreach activities. Effective information security programs must first be grounded in education and training as threats become increasingly sophisticated. GTRI offers a range of Cyber Security Professional Education courses.
This Laboratory's Focus Areas
People
Locations
San Diego Field Office